Atlanta-based Pindrop Launches New Voice Security Tool

Patrons talk in the AUDI amphitheater at Consumer Electronics Show Wednesday, Jan. 9, in Las Vegas. Pindrop made the announcement about its new tool, called Voice Identity Platform, at the show.
Ross D. Franklin / Associated Press
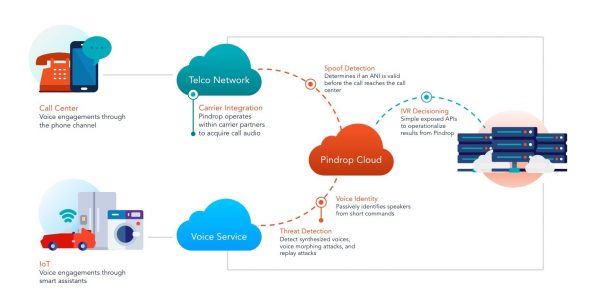
Atlanta-based cybersecurity firm Pindrop, launched a new tool, called Voice Identity Platform, Tuesday.
It can verify if the person asking Amazon’s Alexa to order 1,000 fidget spinners is actually you. The company invented phoneprinting, which is similar to the idea of a fingerprint for your voice.
Pindrop made the announcement at the Consumer Electronics Show in Las Vegas. Software developers will have access to a tool that can help verify a person’s identity by just hearing their voice through a subscription model.
Joshua Soto, Pindrop’s vice president of marketing, said there was a need for it in the industry as more cars, locks and apps are voice-activated.
“If I were to say, Alexa unlock the front door, and Alexa answers back and says what’s your verbal password, anybody that’s in the room or outside my room hears that password, so it obviously creates an opportunity for somebody to exploit it,” Soto said. “You need a high degree of certainty that the person that’s making that request is the person that’s got access to the house.”
The new tool is a big expansion for Pindrop. The company has spent most of the past decade focused on helping identify voice fraud for call centers and eight of the ten largest U.S. banks.
Kennesaw State University information security professor Humayun Zafar said the new tool is a great first step, but it will take time to more fully secure voice transactions and authentications.
“The voice assistant platforms we use currently have massive security holes, they can pick up frequencies humans can’t hear,” Zafar said. “At times the assistants seemingly activate without being asked to. Pindrop may be able to plug some of these gaps and force other vendors to do so as well. In a hyper connected world any one of these vulnerabilities can literally open doors for hackers.”








